In a digital world teeming with hidden dangers, protecting your online presence is crucial. Imagine you’re a traveler in a vast, shadowy forest, where cyber threats lurk around every corner. This story explores how everyday users, like you, can navigate these perils with stealthy defense tactics. From hackers to data breaches, the risks are real and ever-present. By adopting smart strategies, anyone can shield their digital life effectively. The key lies in tools that operate invisibly, ensuring your safety without drawing attention. This narrative connects to your experiences, showing how simple steps can make a big difference in staying secure online.

Building Your Digital Fortress
Users must first build a strong digital fortress against threats. Encryption acts as an invisible shield, hiding your data from prying eyes. For instance, when browsing on public Wi-Fi, unseen attackers wait to strike. Therefore, using tools that mask your IP address becomes essential. This approach keeps your information safe during daily activities. In addition, regular software updates strengthen defenses, preventing vulnerabilities. Everyday scenarios, like online shopping, highlight the need for this protection. Thus, preparing your setup in advance ensures smoother navigation through risky environments. Remember, a proactive stance helps avoid potential disasters later on.


Executing Stealthy Maneuvers
Now, executing stealthy maneuvers involves quick, adaptive responses to emerging threats. For example, rerouting your internet traffic through secure tunnels keeps trackers at bay. However, this requires understanding basic evasion techniques. In everyday life, social media users face targeted ads that invade privacy. Therefore, employing anonymous browsing methods maintains your anonymity. These tactics not only protect personal data but also enhance overall online freedom. In addition, avoiding suspicious links prevents malware infiltration. Thus, integrating these practices into your routine builds long-term resilience. Anyone, from students to professionals, can benefit from such subtle defenses.

Overcoming Persistent Dangers
Finally, overcoming persistent dangers demands consistent vigilance and layered security. Phishing attempts, for instance, can trick even savvy users into revealing sensitive info. In addition, combining firewalls with encryption creates a robust barrier. This story shows how our hero, much like you, defeats ongoing challenges through persistent effort. However, staying informed about new threats is equally important. Everyday users encounter risks in emails and downloads. Therefore, regular scans and backups safeguard your digital assets. By mastering these elements, anyone can emerge victorious in the cyber landscape.
Why NordVPN Stands Out
NordVPN emerges as an excellent choice for stealthy defense in this story. It offers top-tier encryption and a vast server network, ensuring anonymous browsing without complications. Therefore, it effectively shields users from threats like hackers and surveillance. With user-friendly features, NordVPN suits everyone, from casual browsers to remote workers. In addition, its no-logs policy guarantees privacy. Choose NordVPN today and secure your online world. Act now—sign up and protect yourself immediately for peace of mind.
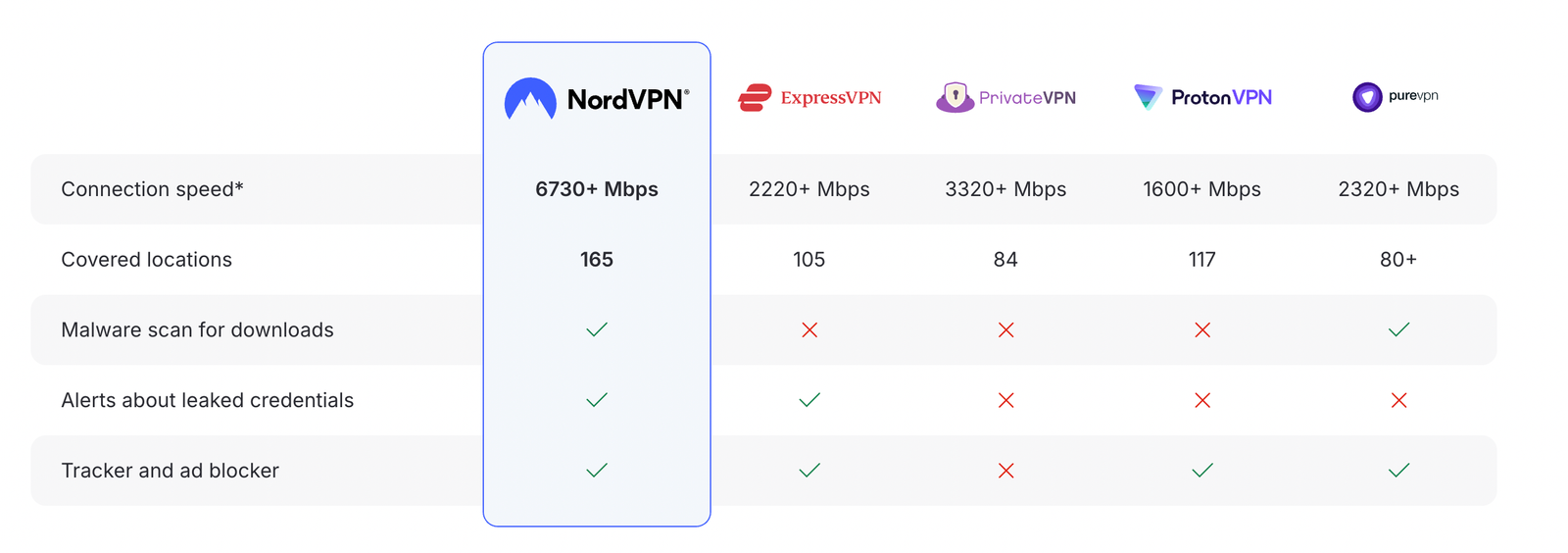
How NordVPN compares to other top VPNs

Disclosure: We earn a commission at no extra cost to you if you make a purchase through links here. This helps support us in creating more content for you. Thank you for your support!







