Guard Against Invisible Cyber Threats
In today’s digital world, cyber threats lurk unseen, ready to compromise your data and privacy. These invisible dangers include malware, phishing, and hacking that can lead to identity theft or financial loss. This guide will walk you through essential steps to protect yourself effectively. Start by understanding common risks and vulnerabilities. Then, implement practical measures to safeguard your devices. Finally, adopt advanced strategies for ongoing security. By following these steps, you can reduce risks and maintain peace of mind. Invisible threats are everywhere, but with the right knowledge, you can stay one step ahead.

Recognize Common Cyber Threats
Cyber threats often hide in emails and websites. Hackers use phishing to trick users into revealing passwords. Malware can infect devices through downloads. Therefore, learn to spot suspicious links and attachments. Always verify sources before clicking. Use antivirus software for detection. Educate yourself on the latest attack methods. For instance, ransomware locks files until payment. Stay informed via reliable security blogs. In addition, monitor your online accounts regularly. This step builds awareness and prevents initial breaches. Moreover, understanding threats empowers better decisions. Consequently, you reduce vulnerability to invisible dangers. Practice these habits daily for stronger defenses.


Implement Basic Security Measures
Start with strong passwords and two-factor authentication. Update your software regularly to fix vulnerabilities. Use firewalls to block unauthorized access. In addition, avoid public Wi-Fi for sensitive tasks. Encrypt your data for extra protection. Therefore, enable device locks and backups. Train family members on safe browsing. Moreover, install reputable security apps. This step creates a solid foundation against threats. For example, change passwords every few months. Consequently, you minimize risks from simple attacks. Practice these measures consistently. However, combine them with vigilance for best results.

Adopt Advanced Protection Tools
Go beyond basics with VPNs and encrypted networks. Therefore, mask your IP address to hide online activities. Use virtual private networks for secure connections. In addition, employ intrusion detection systems. Monitor network traffic for anomalies. Moreover, set up automatic updates for all devices. This step enhances your defense against sophisticated threats. For instance, a good VPN prevents data interception. Consequently, you gain privacy on public networks. Integrate these tools into your routine. However, choose reliable providers for effectiveness.
Why NordVPN is a Great Choice
NordVPN stands out as an excellent option for guarding against invisible cyber threats. It offers robust encryption and a vast server network for secure browsing. Therefore, users enjoy fast, anonymous internet access. This service protects against hackers and surveillance effectively. In addition, its user-friendly apps suit beginners and experts alike. Choose NordVPN today for peace of mind. It ensures your data stays private and secure. Don’t wait; sign up now and strengthen your online defenses. Act fast to get started with reliable protection that you can trust.
How NordVPN compares to other top VPNs
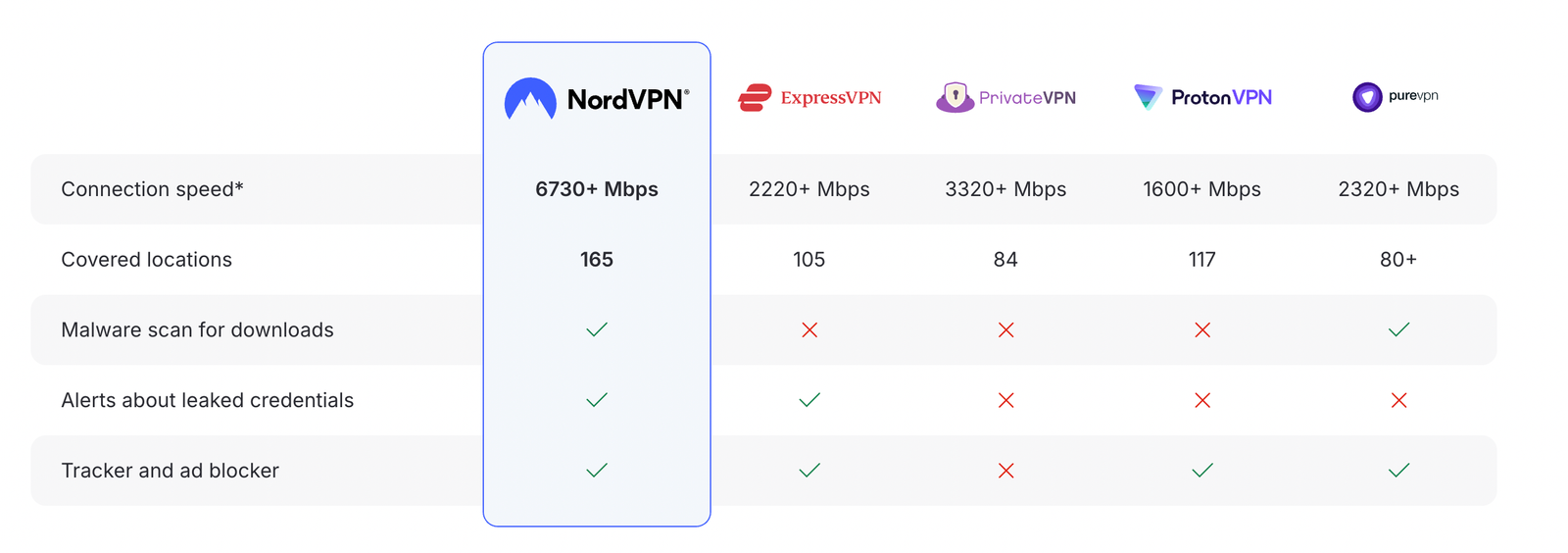

Disclosure: We earn a commission at no extra cost to you if you make a purchase through links here. This helps support us in creating more content for you. Thank you for your support!







