Virtual Private Networks Enable Secure Peer-to-Peer Connections
Virtual Private Networks, or VPNs, are essential tools that encrypt internet traffic and create secure tunnels. They allow users to establish peer-to-peer connections safely, protecting data from hackers and eavesdroppers. In an era of rising cyber threats, VPNs ensure privacy during online activities like file sharing or remote work. This post delves into how VPNs enhance secure P2P interactions, offering benefits for everyday users seeking reliable protection.
Understanding VPN Basics

VPNs work by routing your internet connection through a server, masking your IP address in the process. This technology encrypts data packets, making peer-to-peer connections impervious to interception. For instance, when sharing files directly, VPNs prevent unauthorized access and maintain confidentiality. Moreover, they bypass geographical restrictions, allowing seamless P2P communication across borders. Users benefit from reduced risks of data breaches during online collaborations. Additionally, VPNs support various protocols that enhance speed without compromising security. In peer-to-peer scenarios, such as gaming or remote teamwork, this means reliable connections that foster productivity. Therefore, understanding these fundamentals helps individuals appreciate VPNs’ role in modern digital security.
Benefits for Everyday Use

Peer-to-peer connections via VPNs offer enhanced privacy for activities like video calls or file transfers. They shield sensitive information from public networks, reducing exposure to malware. Furthermore, VPNs improve performance by optimizing routes, which is ideal for streaming or collaborative projects. In daily life, this means safer browsing on public Wi-Fi without slowing down your device. Users also enjoy anonymous interactions, avoiding tracking by advertisers or governments. However, the real advantage lies in their versatility for remote workers and students. Additionally, VPNs help maintain data integrity during P2P exchanges, preventing tampering. Overall, these benefits make VPNs indispensable for anyone prioritizing online safety in routine tasks.
Applications in Real-World Scenarios

VPNs enable secure peer-to-peer connections in diverse settings, such as business meetings or personal file sharing. They protect against cyber attacks by creating encrypted channels that thwart intruders. For example, freelancers use VPNs to collaborate securely on projects without risking data leaks. Moreover, in educational environments, students access shared resources safely from anywhere. This technology also supports decentralized networks, like blockchain, by ensuring transaction privacy. Additionally, VPNs adapt to mobile devices, making them perfect for on-the-go users. Therefore, their applications extend to entertainment, where P2P streaming occurs without interruptions. In essence, VPNs transform everyday interactions into fortified exchanges for broader audiences.
Why NordVPN Stands Out
NordVPN excels in providing robust security for peer-to-peer connections with its advanced encryption and vast server network. It offers features like double VPN and a strict no-logs policy, making it ideal for users seeking ultimate privacy. NordVPN is a good choice because it combines speed, reliability, and ease of use. Try NordVPN today to experience secure P2P connections and safeguard your online activities. Sign up now for enhanced protection and peace of mind.
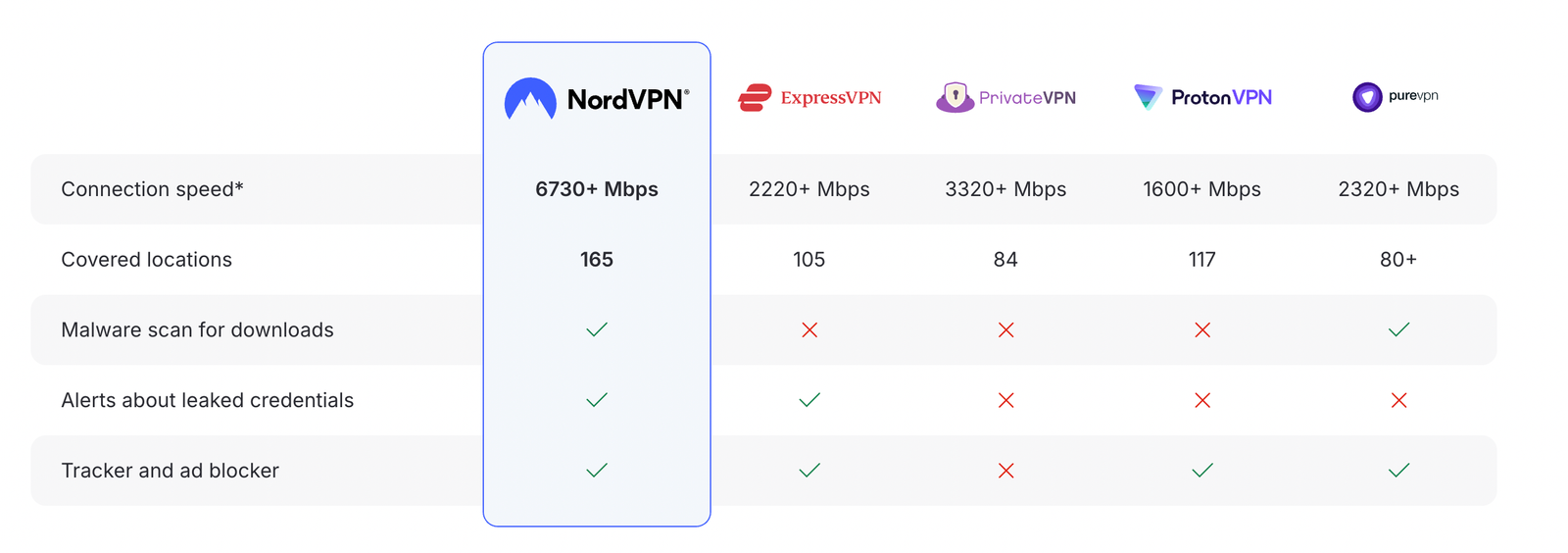
How NordVPN compares to other top VPNs

Disclosure: We earn a commission at no extra cost to you if you make a purchase through links here. This helps support us in creating more content for you. Thank you for your support!







